Salesforce
Salesforce - Leading CRM platform for managing customer relationships and sales.
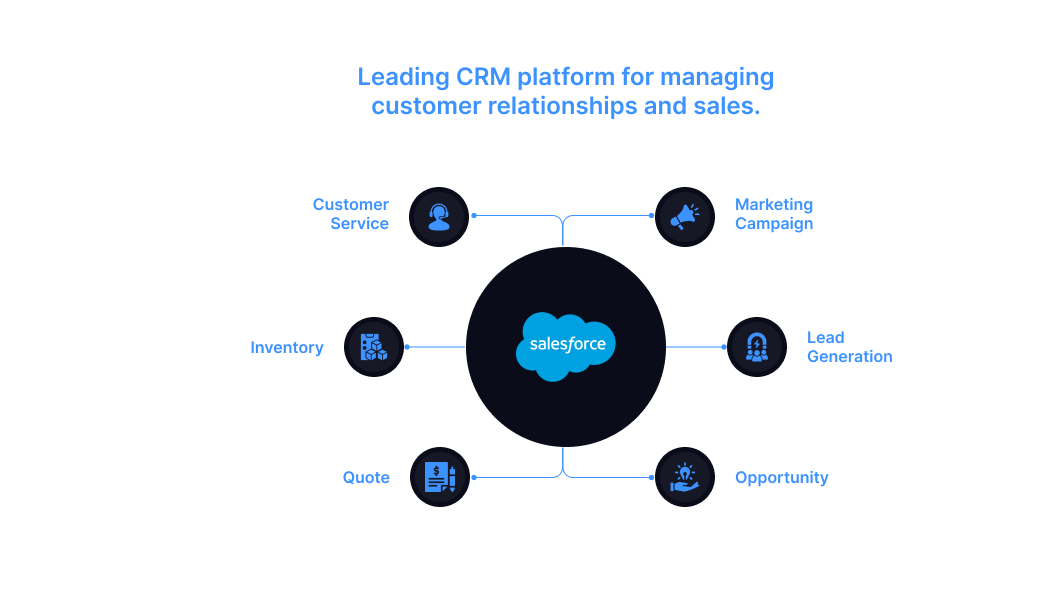
Provider: Salesforce
| Detection Rule | MITRE Tactic | MITRE Technique | Criticality | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
| Suspicious Login Activity | Initial Access | Valid Accounts (T1078) | High | ||||||||
|
|||||||||||
| Phishing Attempts | Credential Access | Phishing (T1566) | High | ||||||||
|
|||||||||||
| Sensitive Data Exfiltration | Exfiltration | Exfiltration Over Command and Control Channel (T1041) | High | ||||||||
|
|||||||||||
| Data Manipulation | Integrity | Data Manipulation (T1565) | Medium | ||||||||
|
|||||||||||
| Unusual Email Activity | Discovery | Account Discovery (T1087) | Medium | ||||||||
|
|||||||||||
| Anomalous API Calls | Command and Control | Application Layer Protocol (T1071) | Medium | ||||||||
|
|||||||||||
| Excessive Permissions Review | Privilege Escalation | Access Token Manipulation (T1550) | Low | ||||||||
|
|||||||||||
APIs and Their Scopes
| Detection Rule | API Required | API Scope |
|---|---|---|
| Suspicious Login Activity | /services/data/vXX.0/query/ | api, full |
| Phishing Attempts | /users/{userId}/messages | Mail.Read, Mail.ReadWrite, Mail.ReadBasic |
| Sensitive Data Exfiltration | /users/{userId}/messages | Mail.Read, Mail.ReadWrite, Mail.ReadBasic |
| Unauthorized Access to Salesforce | /services/data/vXX.0/sobjects/User/{userId} | api, full, refresh_token |
| Data Manipulation | /services/data/vXX.0/query/ | api, full |
| Unusual Email Activity | /users/{userId}/messages | Mail.Read, Mail.ReadWrite, Mail.ReadBasic |
| Anomalous API Calls | /services/data/vXX.0/sobjects/{objectName}/ | api, full |
| Excessive Permissions Review | /services/data/vXX.0/sobjects/User | api, full, refresh_token |
Reports and Widgets for CISO
| Report Name | Widgets | Description |
|---|---|---|
| Login Activity Report | Total logins (daily/weekly) | Overview of user login activities to Salesforce and Outlook. |
|
Failed login attempts Login locations (map visual) |
||
| Email Phishing Report | Count of flagged phishing emails | Summary of phishing attempts detected in user inboxes. |
|
Affected users Email sources (top domains) |
||
| Sensitive Data Exfiltration Report | Count of sensitive emails sent | Instances of sensitive data being sent via email. |
|
Top users sending sensitive data Data types (categories) |
||
| Unauthorized Access Report | Number of unauthorized access attempts | Overview of unauthorized access attempts to Salesforce. |
|
Affected user accounts Time of occurrence (timeline visual) |
||
| Data Manipulation Report | Count of data changes | Changes made to sensitive customer data in Salesforce. |
|
Users making changes Before-and-after comparison visual |
||
| Unusual Email Activity Report | Email volume over time (line graph) | Identify spikes or anomalies in email usage. |
|
Top users by email volume Outlier detection (highlight unusual patterns) |
||
| Anomalous API Calls Report | Count of API calls by endpoint | Monitor API usage and identify any anomalies. |
|
Success vs. failure rate Top users making API calls |
||
| Excessive Permissions Review Report | Count of users with elevated permissions | Overview of user permissions and any discrepancies. |
|
Role changes over time Permissions by user role (bar graph) |