Okta
Human Resources Management (HRM)
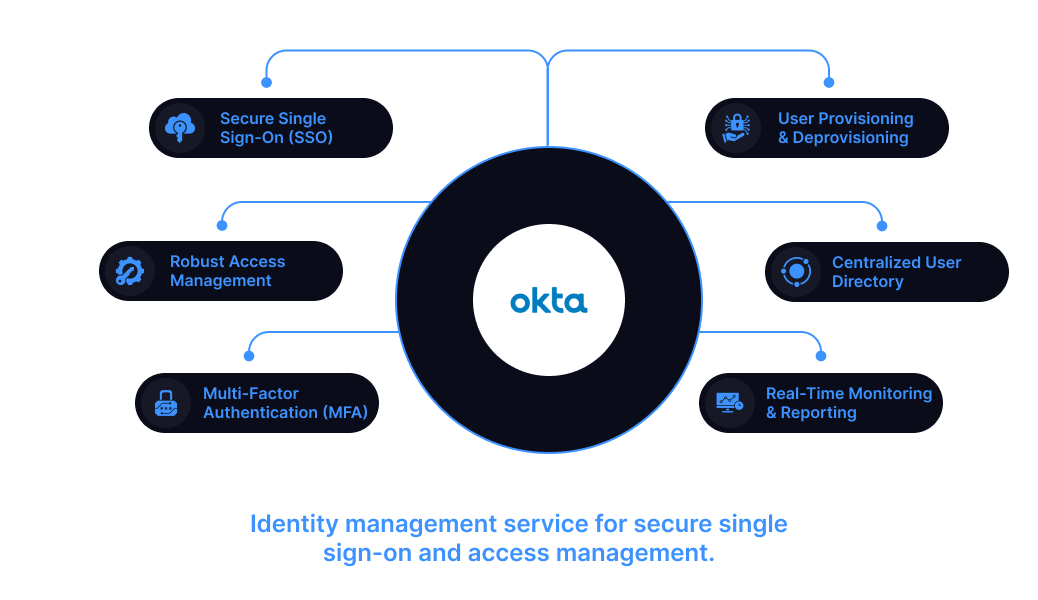
Okta - Identity management service for secure single sign-on and access management.
Detection Rules for Okta
Provider: Okta
| App : Okta | MITRE Tactic | MITRE Technique | Criticality | ||||||
|---|---|---|---|---|---|---|---|---|---|
| Suspicious Login Locations | Initial Access | T1078: Valid Accounts | High | ||||||
|
|||||||||
| MFA Bypass or Failure | Defense Evasion | T1556: Modify Authentication Process | High | ||||||
|
|||||||||
| Excessive Failed Login Attempts | Credential Access | T1110: Brute Force | Medium | ||||||
|
|||||||||
| Access from Unusual Device or Browser | Initial Access | T1078: Valid Accounts | Medium | ||||||
|
|||||||||
| Unauthorized Admin Access | Privilege Escalation | T1078.003: Privileged Accounts | High | ||||||
|
|||||||||
| Multiple IPs for Single Session | Collection | T1021.001: Remote Services | Medium | ||||||
|
|||||||||
| Deactivated User Login Attempts | Persistence | T1078: Valid Accounts | Medium | ||||||
|
|||||||||
| Unusual Access Time Patterns | Persistence | T1078: Valid Accounts | Medium | ||||||
|
|||||||||
| Okta Configuration Changes | Defense Evasion | T1600: Modify System Image | High | ||||||
|
|||||||||
| Suspicious Password Reset Requests | Credential Access | T1078.001: Password Guessing | Medium | ||||||
|
|||||||||
| API Key Abuse or Anomalies | Initial Access | T1078: Valid Accounts | High | ||||||
|
|||||||||
| Bulk User Deactivations | Impact | T1531: Account Access Removal | High | ||||||
|
|||||||||
APIs and Their Scopes
| App : Okta | Required API | Scopes Required | Usage |
|---|---|---|---|
| Suspicious Login Locations | /api/v1/logs | okta.logs.read | Retrieve user login logs and detect unusual locations. |
| MFA Bypass or Failure | /api/v1/users/{userId}/factors | okta.users.read, okta.factors.read | Check for bypass attempts and failed MFA events. |
| Excessive Failed Login Attempts | /api/v1/logs | okta.logs.read | Monitor user login activity and detect high numbers of failed attempts. |
| Access from Unusual Device or Browser | /api/v1/logs | okta.logs.read | Track device and browser information for logins to identify unusual access patterns. |
| Unauthorized Admin Access | /api/v1/events | okta.events.read | Identify changes in admin privileges and log any unauthorized access attempts. |
| Multiple IPs for Single Session | /api/v1/sessions/{sessionId} | okta.sessions.read | Track concurrent sessions and detect multiple IP addresses in a single session. |
| Deactivated User Login Attempts | /api/v1/users/{userId} | okta.users.read | Verify account status and detect login attempts on deactivated accounts. |
| Unusual Access Time Patterns | /api/v1/logs | okta.logs.read | Analyze access time to detect patterns deviating from usual business hours. |
| Okta Configuration Changes | /api/v1/logs | okta.logs.read | Track configuration changes within Okta, especially around security settings. |
| Suspicious Password Reset Requests | /api/v1/users/{userId} /lifecycle/reset_password | okta.users.manage | Monitor and verify the frequency of password reset requests. |
| API Key Abuse or Anomalies | /api/v1/apps/{appId}/tokens | okta.apps.read | Track API key usage patterns and identify possible abuse. |
| Bulk User Deactivations | /api/v1/users | okta.apps.read | Review recent user deactivations and confirm authorization for bulk actions. |
Reports and Widgets for CISO
| Report Name | Widgets | Description |
|---|---|---|
| Login Activity Overview | Total Logins | Summarizes login activity, highlighting failed login attempts and geolocation of suspicious logins. |
|
Failed Logins Suspicious Logins by Location |
||
| MFA Success and Failure Rates | MFA Success Rate | Tracks multifactor authentication trends, identifying potential MFA bypass and geolocation of MFA failures. |
|
MFA Failure Rate by Location MFA Bypass Attempts |
||
| Access Patterns by Device/Browser | Devices with High Login Volume | Analyzes login attempts by device and browser, flagging unusual device/browser patterns. |
|
Browser Usage Trends Unusual Device Access |
||
| Administrative Changes | Recent Privilege Escalations | Reports on administrative actions, particularly unauthorized access attempts or unexpected privilege escalations. |
|
Role Changes by User Unauthorized Admin Logins |
||
| Deactivated and Suspended Users | Deactivated User Access Attempts | Shows login attempts by deactivated or suspended users, providing insights into potential policy violations or insider threats. |
|
Suspended Accounts Activity |
||
| Unusual Access Times | Logins Outside Business Hours | Highlights access attempts that occur outside of normal business hours or other access anomalies. |
|
Time-based Access Anomalies |
||
| Configuration Change Logs | Recent Okta Config Changes | Monitors configuration changes in Okta, particularly security-sensitive settings such as password policies and MFA configuration. |
|
Security Setting Modifications |
||
| API Key Activity | API Key Usage by IP | Tracks usage of API keys, including geolocation and request volume to detect anomalies or abuse. |
|
High-Volume API Requests Unauthorized API Key Access |
||
| Bulk Actions Monitoring | Bulk User Creation | Displays any bulk changes in user provisioning, such as mass deactivations, to ensure that these actions are authorized and not signs of misuse. |
|
Bulk User Deactivation Group Assignment Changes |
||
| Password Reset and Account Recovery | Password Reset Attempts | Monitors frequency and success rate of password reset and account recovery requests, helping identify account compromise attempts. |
|
High Frequency Password Resets Account Recovery Success/Failure Rate |